Oh, my AI, what can be done? There’s lot of FUD (fear, uncertainty, and doubt) being spewed from the stages of conferences. But over here in the trenches we are the more practical sort. This isn’t just policy; it’s day-today IT and cyber security using Microsoft 365 Business Premium.
What we need to know
- Who is using AI?
- Which AI are being used?
- Which ones do we want to allow?
How to monitor AI use
We’re going to use two built-in tools to help us monitor AI use in our network.
- Entra
- Defender for Cloud Apps
Both of these are included in the Microsoft 365 Business Premium license.
Configure User OAuth Consent
Let’s start with Entra. How do permissions for data access get granted to AI? Via OAuth. The problem with OAuth permissions is that they never expire, so once a user has responded to the request for access, that permission is granted FOREVER from that service to your network. Therefore, we need the admin to make a decision on whether this is reasonable or not.
Below is what these types of requests look like. They could contain a longer or a shorter list of permission requests. It depends on how the AI is going to help you. Does it help you write better? Then it probably is going to ask for access to your files.
Notice that your users can also grant permission for this AI to your entire organization, not just for themselves. That should give you a shiver.
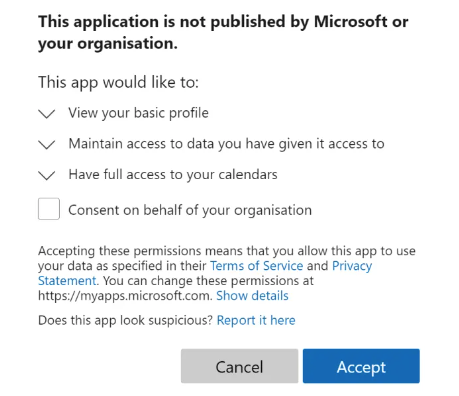
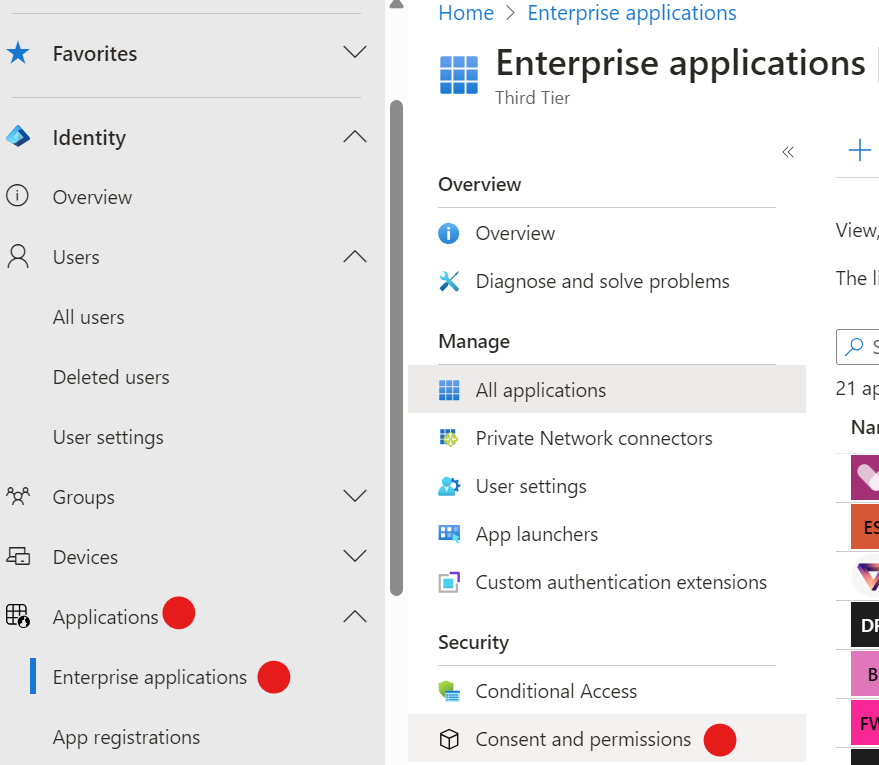
Let’s put some reasonable controls around this. Open https://entra.microsoft.com/, then following the red balls in the screenshot below, select Applications, Enterprise applications and finally Consent and permissions in the sub-menu.
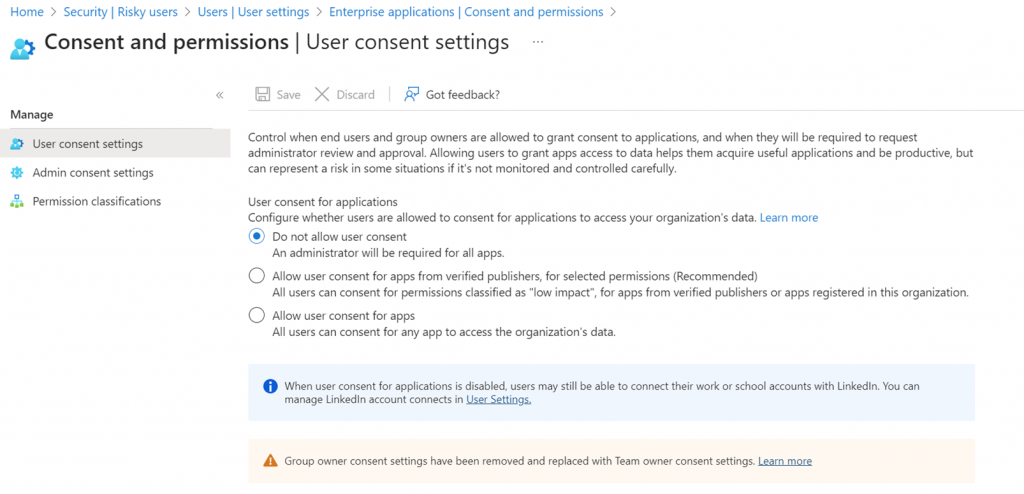
Here we’re going to configure this so that users must request admin permission to provide permissions for an app, in our case AI, to access data.
In the User consent settings, select Do not allow user consent. This will cause the user to see a message that sends a request to the admin to approve the requested access to data.
Next, move down the menu to Admin consent settings. Here you will select all of the Yes options as seen in the screenshot below. In the Reviewer type section, you will choose the email address where you want the users request for permission to go. This can be a single admins email address or several. It can also be an email address that sends the request to your RMM.
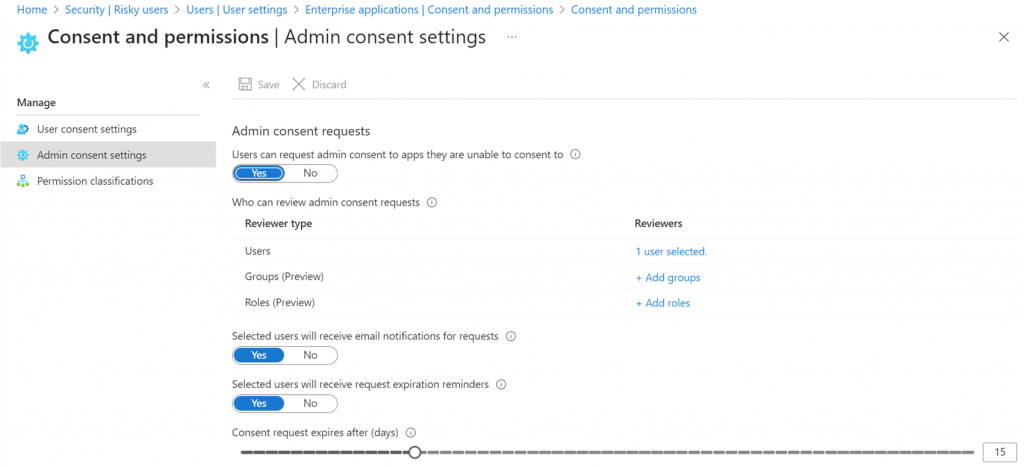
Lastly, as shown above you need to set a time frame in which the admin will respond to the request. After this time, the request for permission will expire.
Monitor and block for unauthorized AI
Next, we’re going to set up a policy to alert us to the Generative AI use in our network. We will use Defender for Cloud Apps. Open https://security.microsoft.com/.
Scroll down the menu to Cloud Apps and expand Policies. Then click Policy management and create a new policy. You can use a blank template or the Collaboration app compliance check. Either is fine.
As shown in the screenshot below, give your policy a name, select the severity level, provide a description and configure the matching category. Microsoft maintains the list of what is considered Generative AI. Last week the list was 218 items, this week it is 454 unique generative AI’s long. It will get longer and longer.
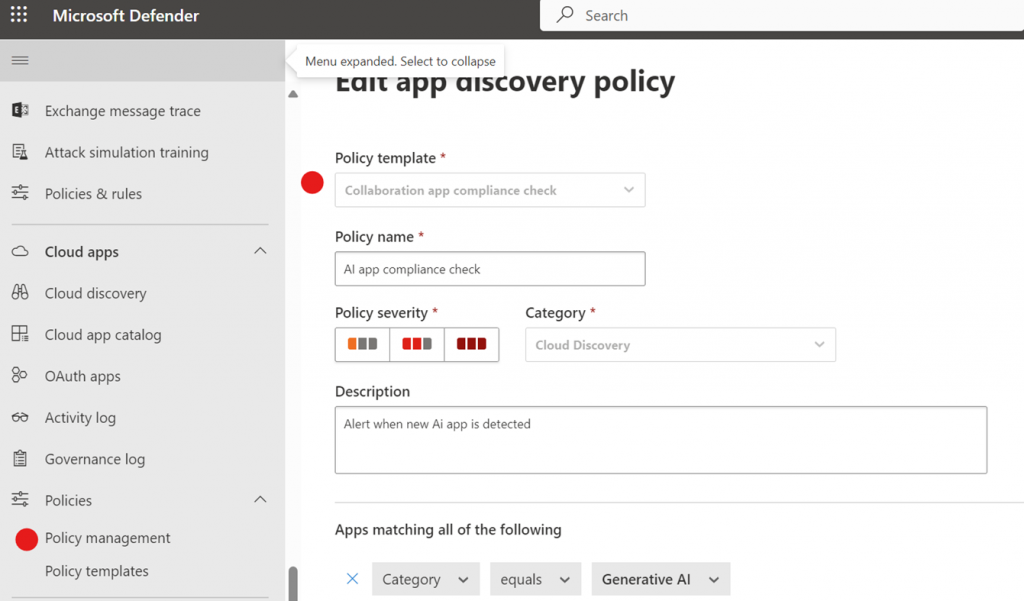
Continue through the template to configure where you would like the alerts that this policy will generate to be delivered.
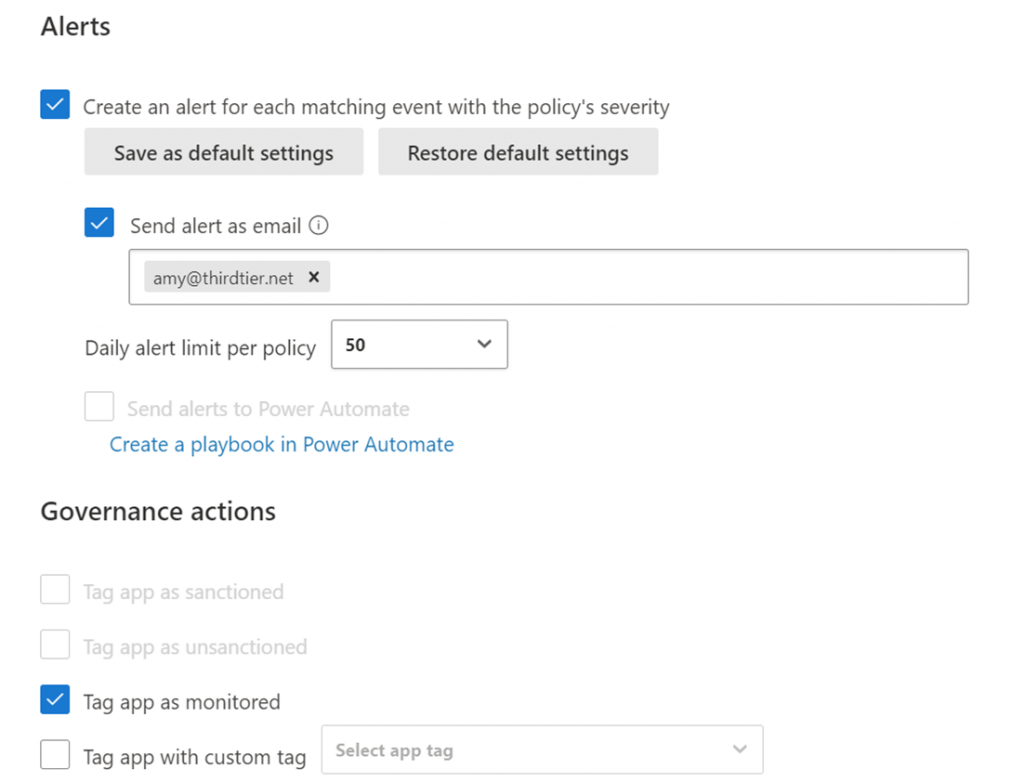
The final thing that you need to configure is what to do when a new AI is discovered in your network. At a minimum, you want to tag it as monitored, as shown above. But most will want to tag the app as unsanctioned. An unsanctioned app is a blocked app. A monitored app will present an error message but will allow the user to continue with the AI usage.
Which apps have been approved?
It is very likely that you’re playing catchup with this permissions issue, so which apps have been approved? You can find out in Defender under Cloud Apps by selecting the Oauth apps menu item.
What you see here is a list of Oauth apps that have access to your data. Browse through the list. Click items to determine who approved this app and when they last used it. Manage access by click the Check to note your approval or the circle with the line through it to block that app. See the sample below.
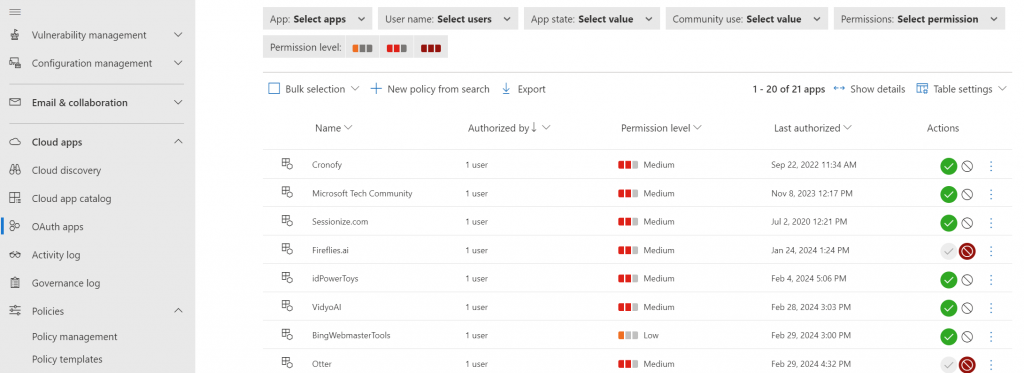
Now we know, who is using AI, what access has been granted and how to manage AI use going forward.
All we do is support IT professionals. Help for IT Pros, M365 admin News, Security community, peer groups, MSP training and more. https://www.thirdtier.net




