Microsoft is moving from MFA (multi-factor authentication) settings to MFA policies. They have also improved nearly all of the MFA and SSPR (self-service password reset) options. There’s mandatory migration underway and you have until later this month to get them into place voluntarily or Microsoft will do it for you. Don’t let your clients be surprised! Get ahead of this change. Microsoft has even built a migration procedure for you.
What does this mean for the end user?
It means less confusion about what they setup for authentication for resetting their password and what they use for MFA. It also means more modern secure MFA methods. All of the items have been updated and users will notice the changes in appearance of the MFA prompt.
Migrate from settings to policies and adopt the new improved authentication methods
What follows is the policy settings and options that I have chosen. Whether you decide to choose what I have chosen or follow your own path, the steps will be the same.
Update the SSPR settings
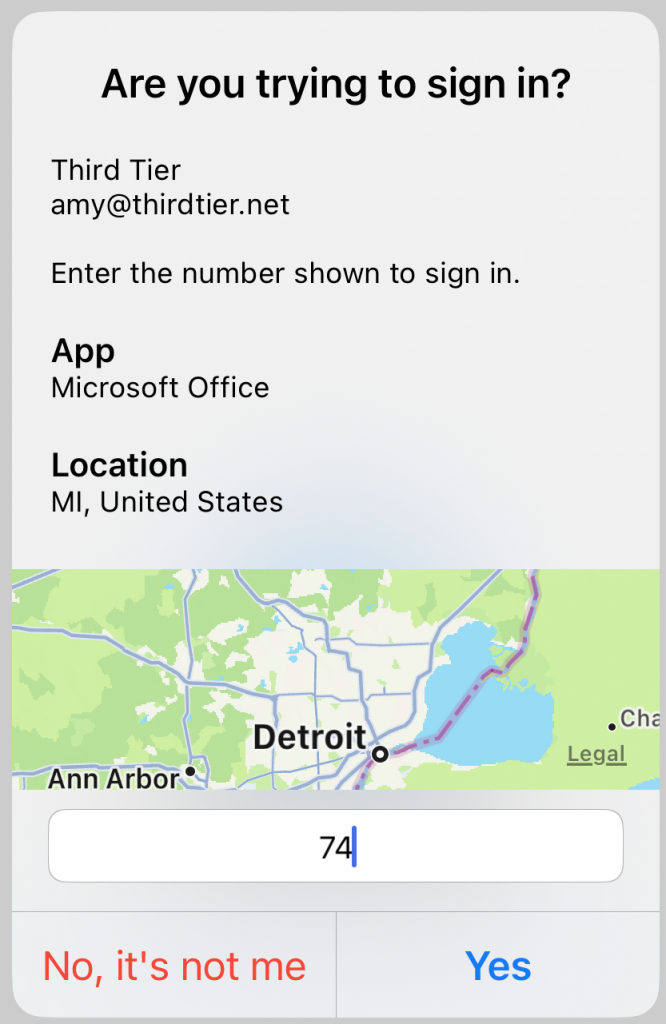
Step 1: Go to the Azure AD portal, click on Password reset. Click on properties. Make sure that self-service password reset is enabled for All.
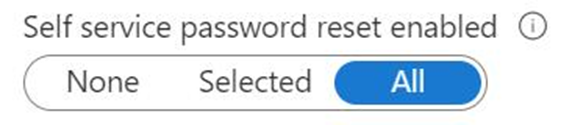
In the same area, to go Authentication methods. Uncheck all except this one.
Remove old MFA settings
Step 2: Go back to the Azure AD portal, and this time navigate to Security
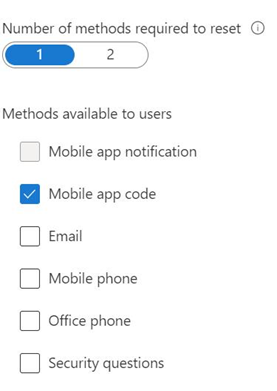
- Click into Multi-factor authentication, then in the main pane click the item list under Configure then Additional cloud-based multifactor authentication settings. You want everything here off, however, you will have to leave one item checked, notification through mobile app. Once you complete the process this final box will be unchecked.
Assign new policies
Step 3: Go back to the Security section. This time click on Authentication Methods.
Assign the policies for each type of authentication to the groups that require it. Be sure to also look in the Configuration tab for each. Note that each has an option that allows it for password reset or login. Before we had separate settings for each, now they are combined.
Microsoft Authenticator settings
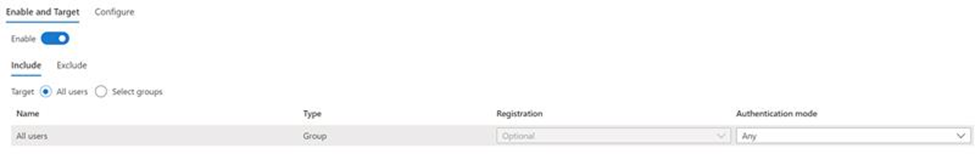
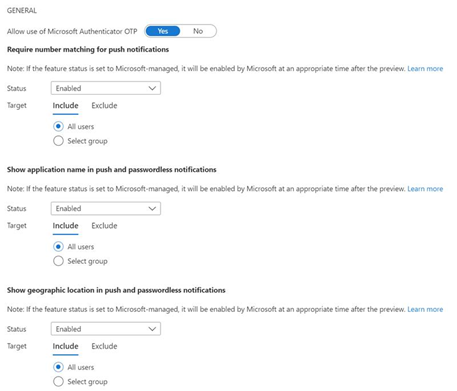
SMS Preview settings
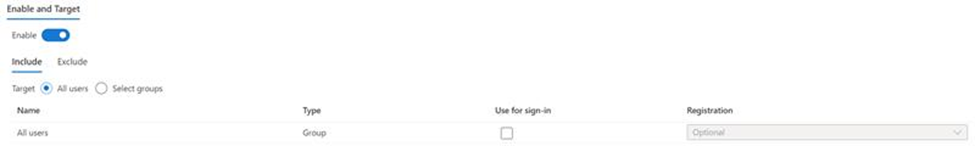
Temporary Access Pass settings

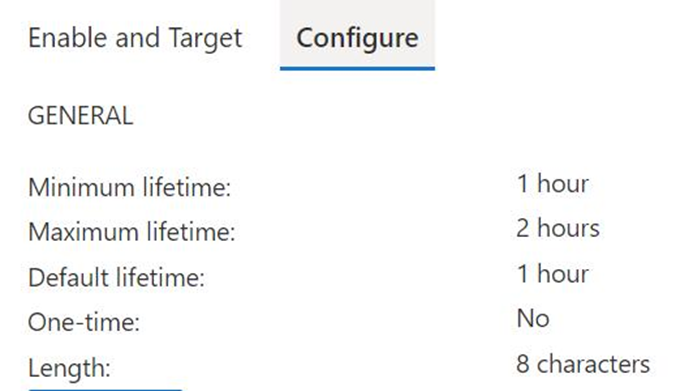
Email OTP Preview settings
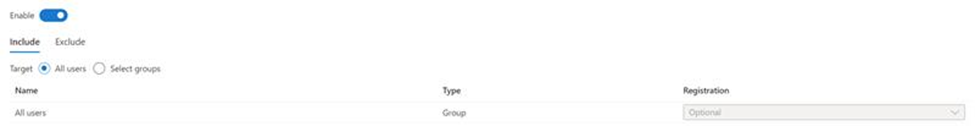
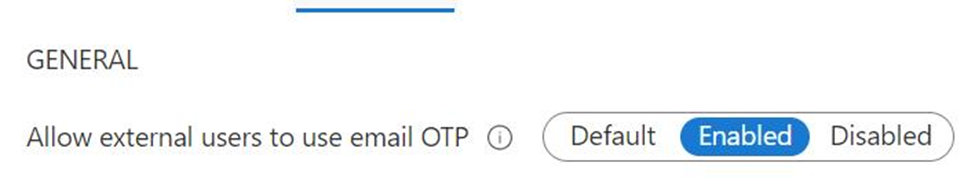
Review the new policy
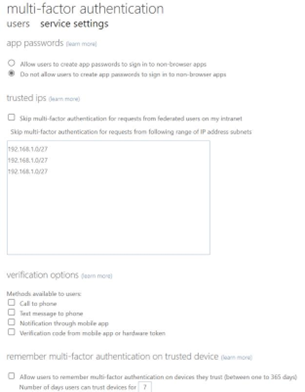
Once you have completed creating your authentication policy, it will look similar to the figure below.
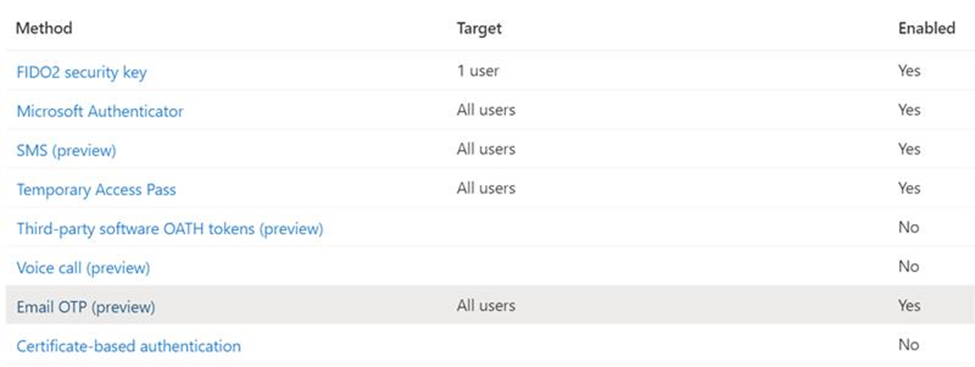
Move the migration forward
At the top of the screen, click on Manage Migration and set to Migration In Progress. This is essentially a test phase where your legacy policies, if any, are still respected. Microsoft is scheduled to complete this migration by the end of February. At that time, you could move this forward to Migration Complete.
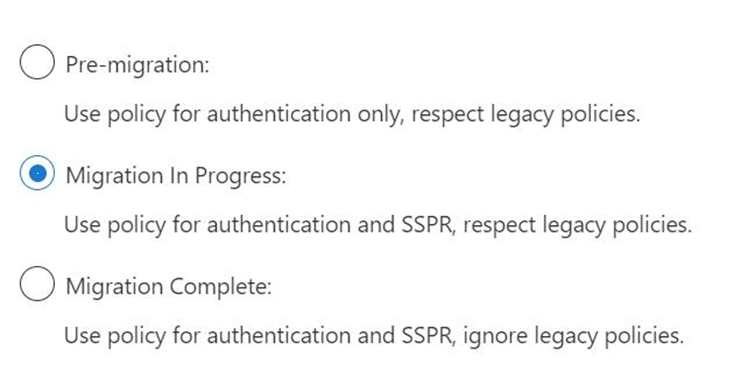
Finally go back and verify that the last checkbox is unchecked in step 2 above.
Read more about Azure AD in our blog.
All we do is support IT professionals. Microsoft 365 technical assistance, Newsletter, Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, Kits, papers, Business consulting and more. https://www.thirdtier.net




5 thoughts on “Migrate to the new MFA authentication policies”
We have 100 clients to do this for. Do you know where I can find the commands to do this in Powershell?
Sorry i do not. It may be graph rather than powershell. Most new things are. I would consult Microsoft learn.
Nice, but what about the security questions for SSPR?
They are no longer in play