Finally, there is an easy way to deploy a base set of conditional access policies to users, devices and apps in a tenant. Microsoft calls it Conditional Access Templates and you will find them in Azure AD – Security – Conditional Access – Conditional Access Templates.
Conditional access is a significant security aid. By setting policies to control, who, when, where and what any person can access you’ll greatly enhance security.
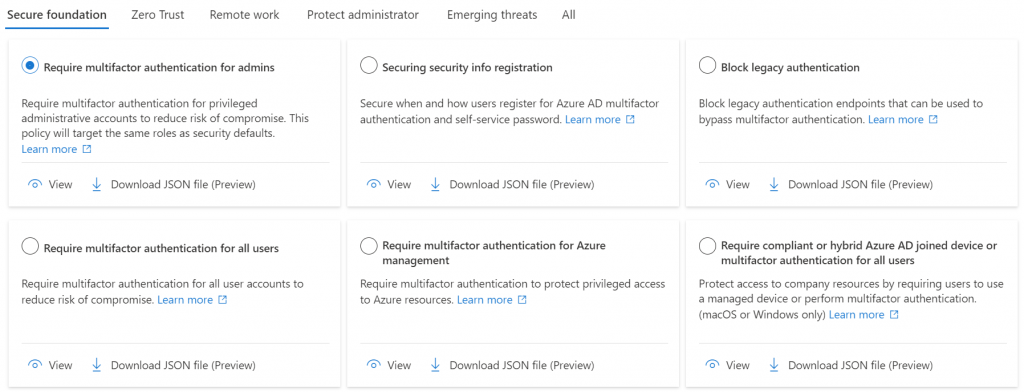
There are currently 5 categories of templates, as seen in the figure above. These are Secure Foundation, Zero Trust, Remote work, Protect administrator and Emerging threats.
Prerequisites for conditional access templates
In order to make use of any of the features of Azure AD, you need to first configure the basics.
You’ll want to have:
- devices registered or joined (preferred)
- users assigned to groups
- devices assigned to groups
User groups should include departments, job roles or locations. Device groups should include mobile, desktop, location specific, corporate owned, employee owned, tablets, joined, registered, unmanaged, etc. The sky’s the limit and the needs of each company will vary.
Things to know about all of the conditional access templates
- If you click View, you will see exactly what the settings of the policy are
- If you want to push this policy using a tool, then click to download the JSON file and then import it into your management tool
- When you enable the template to create a policy, it is created in Report only mode so you can evaluate the impact of the policy on your tenant.
- Nearly all policies will exempt the user that is creating the policy from the policy. In many cases, this will not be what you want. Perhaps you want to exempt a break-glass account from policy, but you probably don’t want to exempt your daily admin account.
Replicate security defaults
The easiest place to start is to replace Azure AD Security Defaults with conditional access. The two are incompatible with each other. Meaning, if you are going to use conditional access, then you can’t use security defaults.
- Block legacy authentication
- Require multifactor authentication for admins
- Require multifactor authentication for all users
- Require multifactor authentication for Azure management
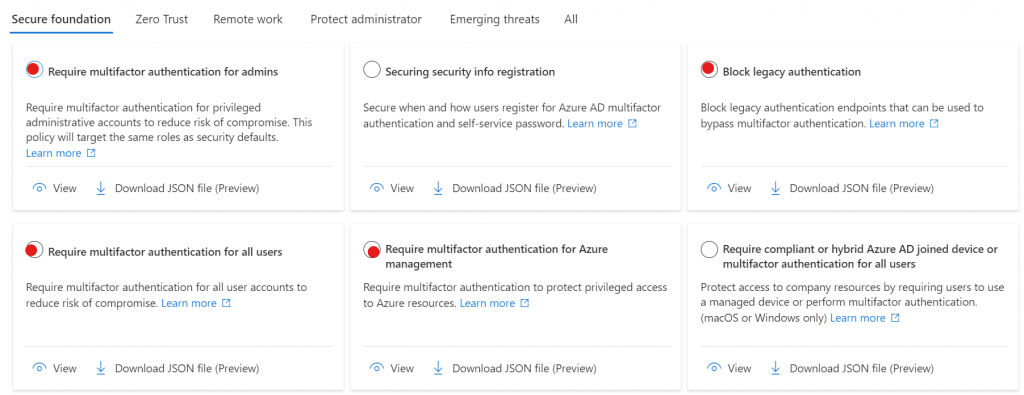
The four policies above are the ones that replicate security defaults. These are found in the Secure foundation category and are the ones I’ve highlighted below with the red dots.
Creating a policy from a template
To create a policy from any of the templates you’ll first select the template, then press the Next: Review + Create button at the bottom on the page.
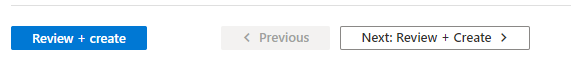
Alternatively, you can press the Review + create button which skips right to the end of the configuration and creates the policy with all of the defaults. For some policies this works just fine because there are no configuration options. However, as you enable more advanced policies you’ll want to step through the process. I recommend getting into the habit of using the Next: button.
For example, choose to create a policy from the Require multifactor authentication for admins template. Then press the Next: Review + Create button.
You are now presented with the policy to review. You’ll notice that your only option to edit the items in the basic category.
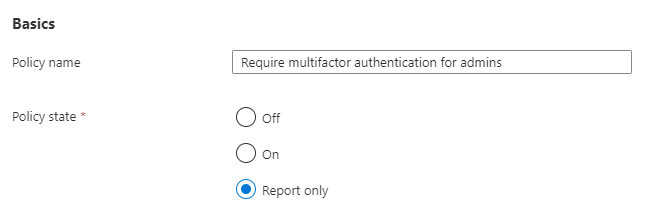
In the case of these four security defaults replacement policies, you will probably want to set them to On, rather than Report only so that you do not leave a gap between the security defaults you’ve been operating under and your new conditional access policies.
Create the four security default policy replacements taking care to set the exempt account as you want it for the tenant.
Look for additional articles on configuring Azure AD conditional access from templates in other blog posts on the topic at the link below. This is the first article in the series as of February 2023.
Read more about Azure AD in our blog.
All we do is support IT professionals. Microsoft 365 technical assistance, Newsletter, Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, Kits, papers, Business consulting and more. https://www.thirdtier.net




