Continuing with our series to implement the tasks outlined by Threat Analytics in Microsoft Defender, today we will review what needs to be done to protect the network from participating with Qakbot, one of the most notorious ransomware vehicles out there.
Microsoft suggests:
- block unknown malware and all future deliveries of it
- prevent office form launching child processes
- use the advanced protection against malware configuration
- enable cloud delivered protection
Block unknown malware
In Defender, navigate to Email & Collaboration, Policies and rules. Select Threat policy, then Safe attachments. Create or modify your safe attachments policy as shown in the figure below.
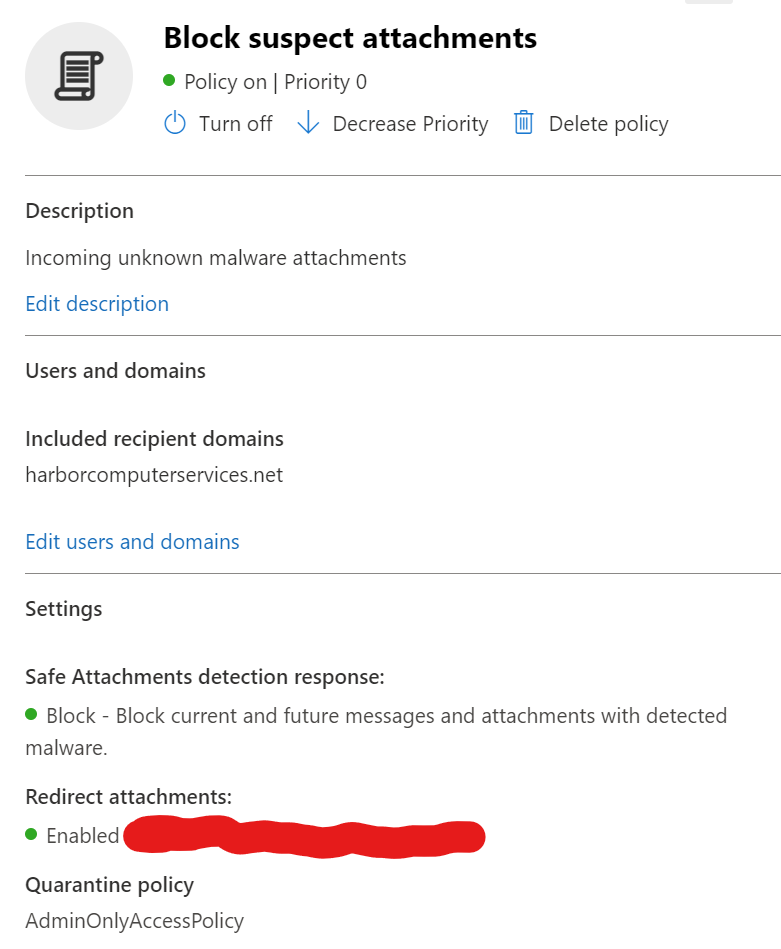
Above the important settings are to select your email domain, set the action to Block and enable AdminOnlyAccessPolicy for the Quarantine policy. This will mean that only an administrator will be able to release the malware attachment from quarantine.
Choosing to redirect the attachments to another location is optional. I do it for ease of availability of the file should we need to detonate it into a safe walled environment. This is not necessary for everyone.
Prevent office from launching child processes
To enable this protection launch Intune, then navigate to Endpoint Security and Attack surface reduction. This is where you will configure your rule or rules. If you need to segregate rules by groups of devices, then you’ll have more than one. If you are in position to apply a single rule to all machines, then do so.
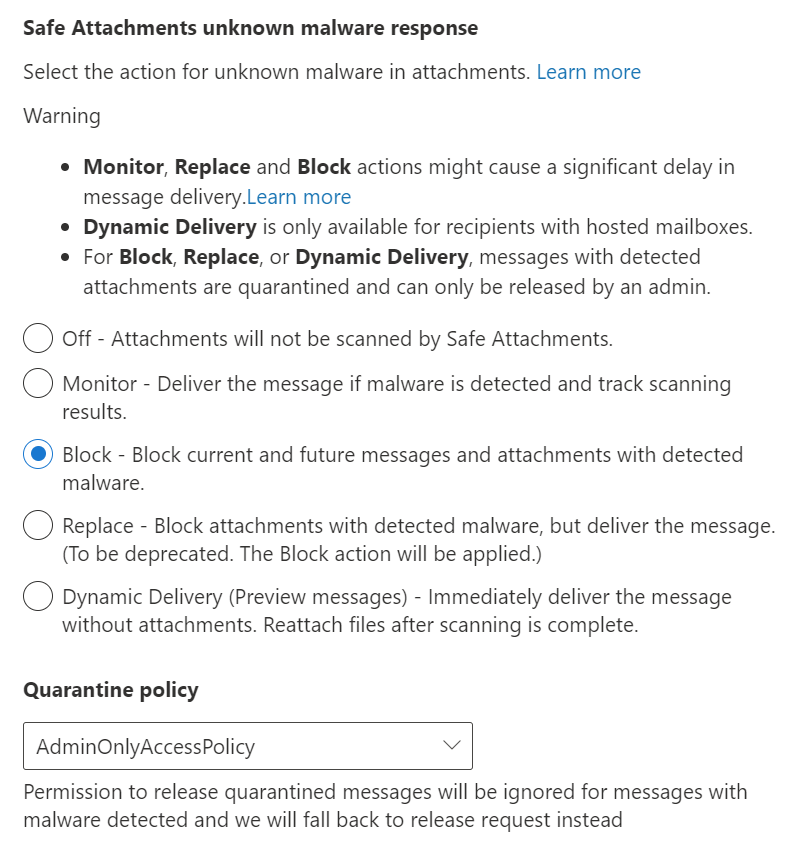
Click the + to create a policy. The figure below is the policy that is required for this configuration.

Of all of the Attack surface reduction policies, this is the one that is often the most problematic for the end user. Some have developed scripts that are required for their work process that will not allow them to have this policy. If that is the case, determine how critical that process really is, because this is a serious and common means for malware to use to do its dirty work. If it cannot be avoided, then you’ll need to make an exception for that user.
Use advanced protection against ransomware
In Defender, navigate to Endpoints, Vulnerability management, Recommendations. Then search for the word Ransomware. This will bring up a short list of options. Choose Use advanced protection against ransomware.
Here you’ll find that it suggestions three items to configure.
- Ensure that Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled.
- Ensure that Cloud-delivered protection is enabled
- Enable this ASR rule in Block mode using either MEM (Windows 10 only), Group Policy or MDM
Turn on Defender Antivirus with real-time protection
As described in this article, Manage Microsoft Defender Antivirus in your business | Microsoft Learn, there are five options for how to push this configuration out to your devices. We will use the Configuration policy option.
In Intune, navigate to Endpoint Security, then Antivirus. Create a new policy, give it a name, select the OS it will apply to and then configure it for your environment as in the figure below. Assign to the All Users group or a specific group of users if you are adjusting security for particular groups of users.
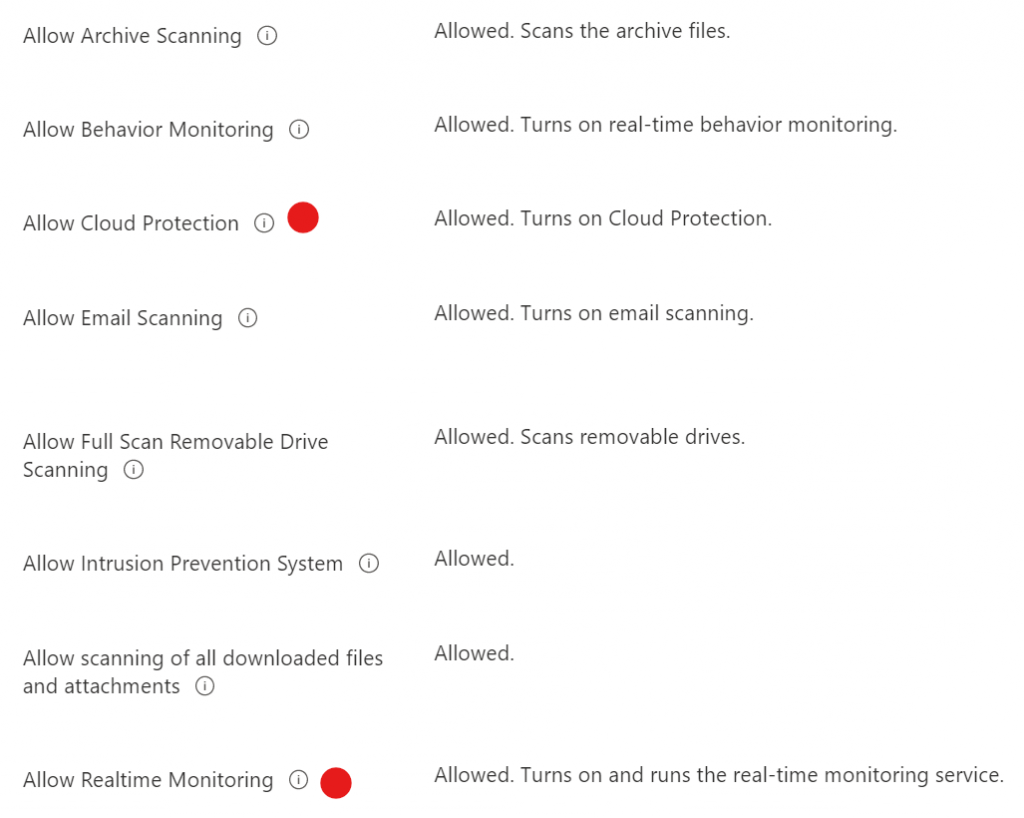
For the purposes of configuring the specific protection that we are working on, the red dots indicate the required settings, but you should configure as many of the protections within a single policy as possible.
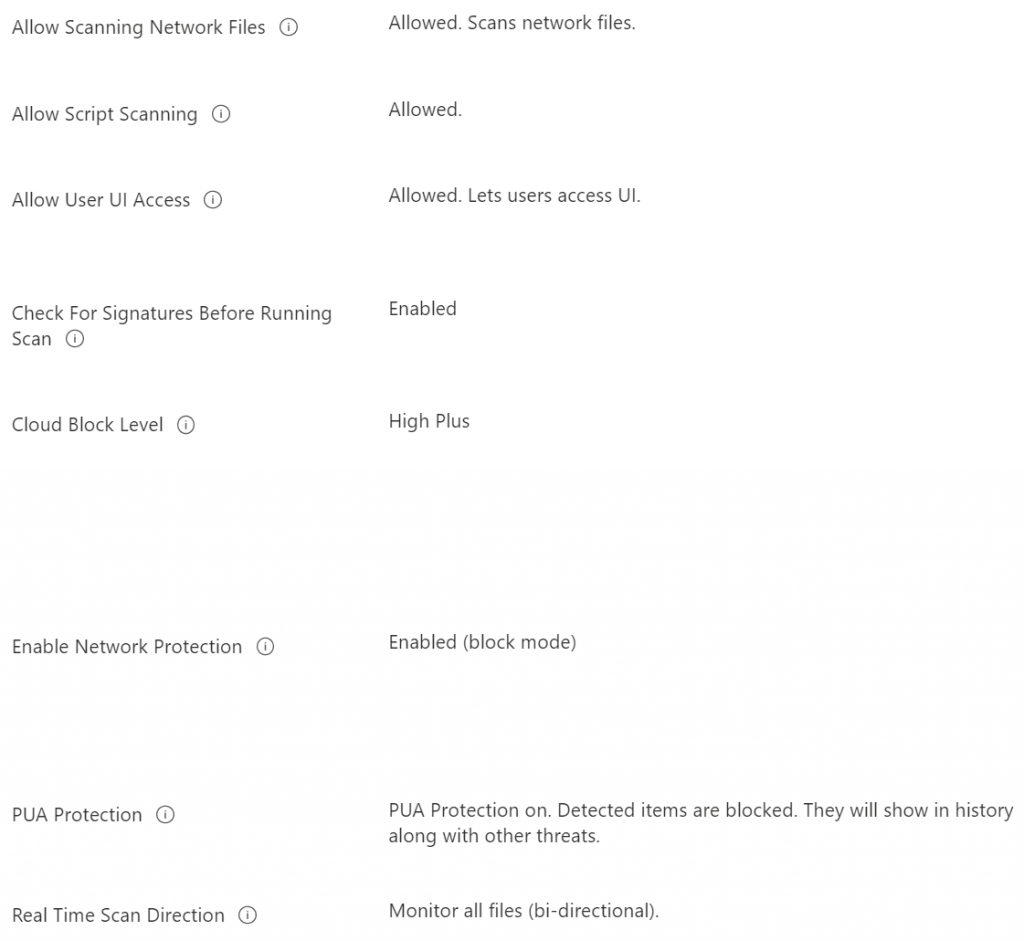
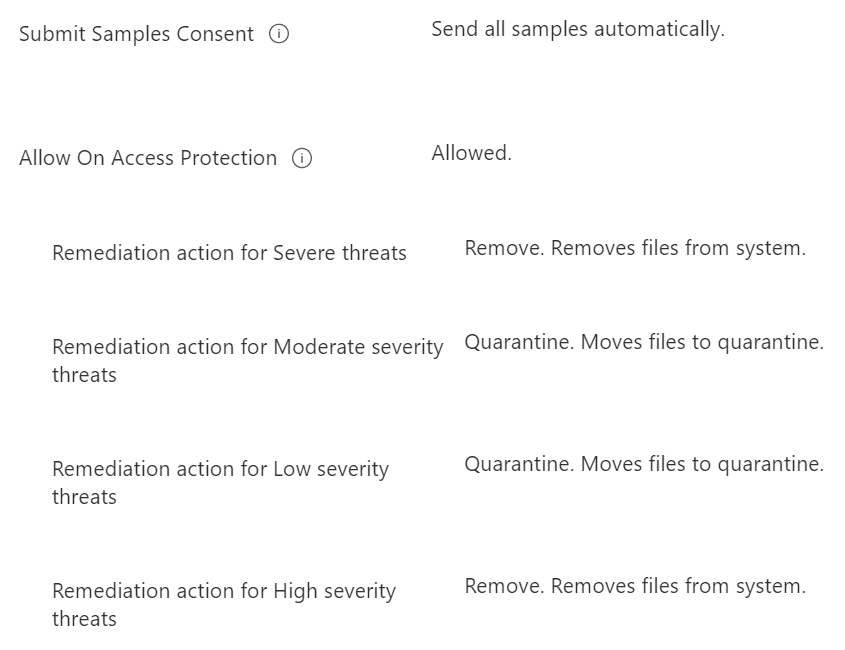
By enacting this policy we have completed all of the requirements for disrupting Qakbot. All it took was an email attachment policy, a little hardening of Microsoft Office and the configuration of the built-in anti-virus software.
If you’d like to read more about configuring Defender we’ve consolidated them for you here
All we do is support IT professionals. Microsoft 365 technical assistance, occasional Newsletter, Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, Papers, Business consulting and more. https://www.thirdtier.net and https://www.facebook.com/thirdtier for the community groups listed above.