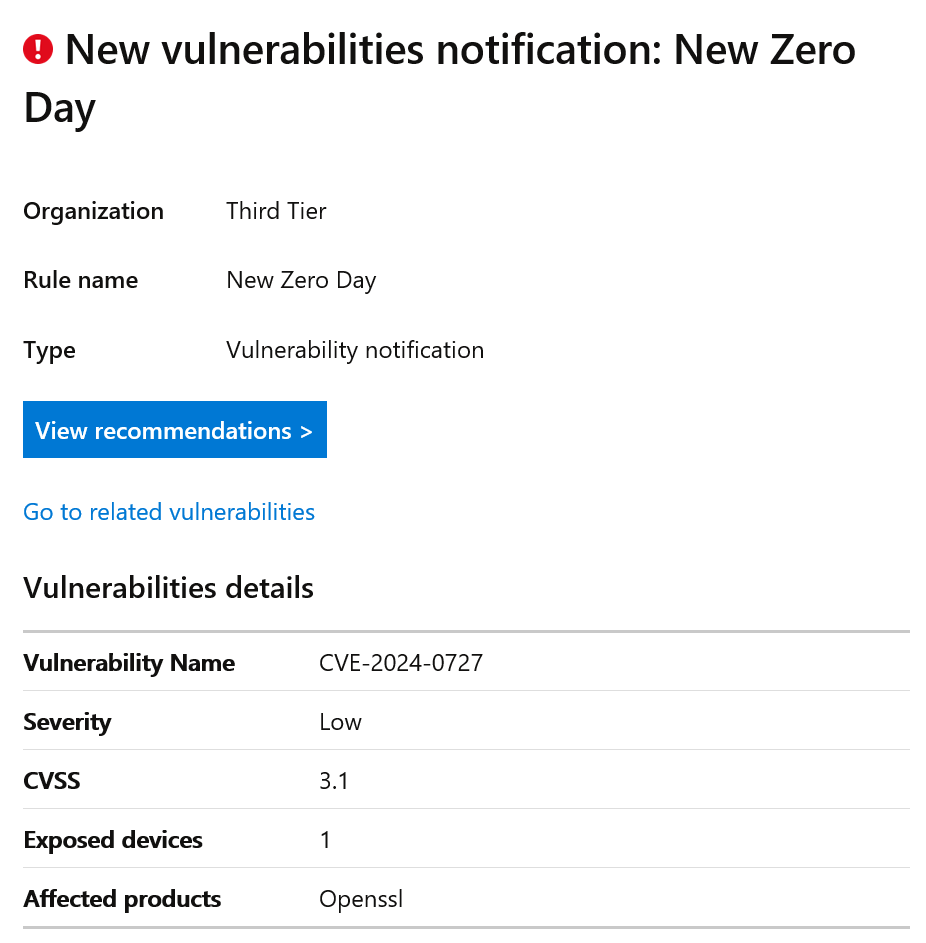
Microsoft Defender Vulnerability notifications sent an email informing about a new zero-day in Open SSL. I don’t use Open SSL intentionally so how am I subject to this zero-day? We’re going to use Defender to find out and then remove the vulnerability.
Find the problem application and associated files
The question to answer is which of the products that I use, contain this vulnerability? Let’s click on the View recommendations button and find out. Moving to the Vulnerable files tab provides the fastest way to the answer. Zoom contains the dll’s affected by this zero-day. I checked for an update in Zoom and there wasn’t one yet.
If you’re not starting from the vulnerability email, then go to security.microsoft.com, the home of Defender, expand Endpoints, Vulnerabilities and Recommendations. This is where you can find the most current list of vulnerability alerts for your company.
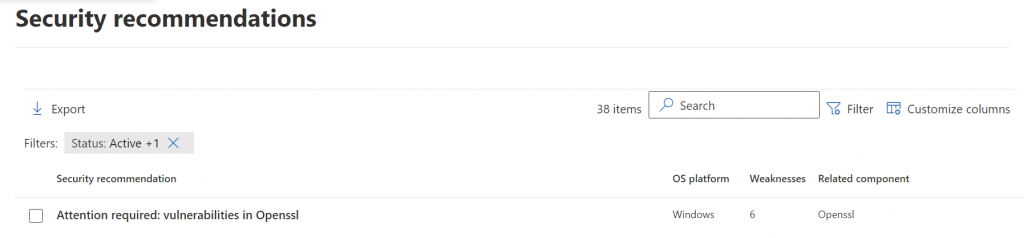
If you are starting from the email, then you’ll be brough straight into the vulnerability section of Defender, where you can begin to take action.
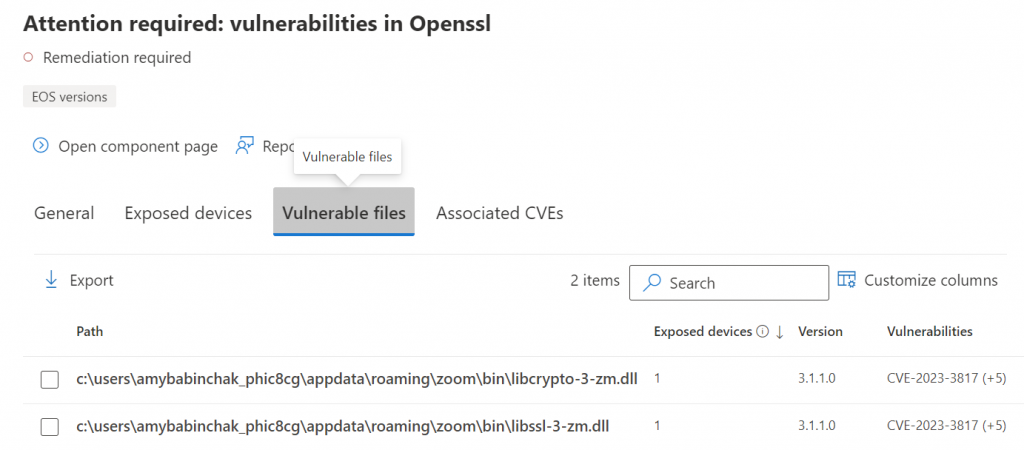
Delete the files
Since there isn’t an update I can apply yet, I use the Vulnerable files tab to provide me with a list of where the files are in my network that I need to delete. This will likely break zoom for the time being. I’ll have to be aware that if I enter another zoom meeting before the update is available that they may very well return to my computer. I’ll make sure to prioritize the installation of updates from Zoom.
Using the path provided, the files are easily deleted. You can do this manually if it’s just a computer or two, or you can use your RMM tool to remove them. Since it’s an application path the storage location will always be the same.
All we do is support IT professionals. Security community, MSP Legislation community, Intune, Defender and Lighthouse community, Peer groups, courses, papers, Business consulting and more. https://www.thirdtier.net




