I’ve covered this in several of my classes but today I realized that I hadn’t blogged it. So here we are. There are a couple of simple settings in Entra ID that will help you prevent Shadow IT from giving permissions to cloud apps.
Manage applications
Log into https://entra.microsoft.com/ with an admin account. Expand Application and select Enterprise Applications. Now choose Consent and permissions from the menu.
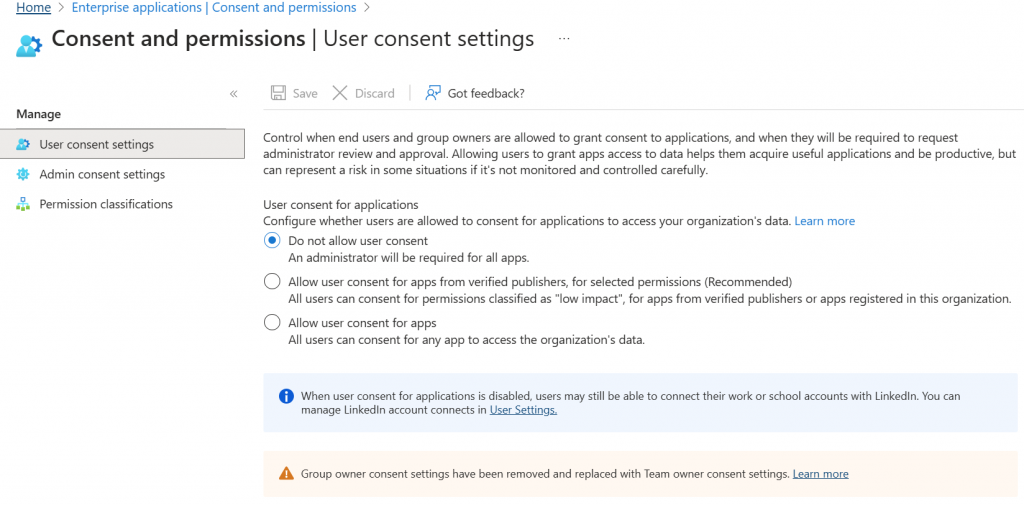
The default setting here is to Allow user consent for apps from verified publishers, for selected permissions (Recommended) That is Microsoft’s recommendation.
However, my recommendation is to select Do not allow user consent. Why?
Because while users understand that they need an app to help them with their job, they don’t understand the security implications of giving permission to an oAuth application permanently. Once the permission has been granted it is there forever.
A second reason is that most businesses have communication issues. One user installs an app and sets if up for corporate use, and another employee has no idea that it’s available to them and sets up a different app that does essentially the same thing. The network is now over permissioned and has an app sprawl problem.
How do apps get permissioned now that I’ve blocked them?
When a user wants to use an oAuth app, they will be blocked from doing so and a message will appear asking them if they want to ask the admin for permission to use this app. The admin will receive an email informing them of the request and can then make the decision on whether this app is redundant in the network, requires only acceptable permissions, and has a good reputation. Then the admin grants permission to the app and allows the app to gain the permissions it requires.
This is configured in the Admin consent setting window.
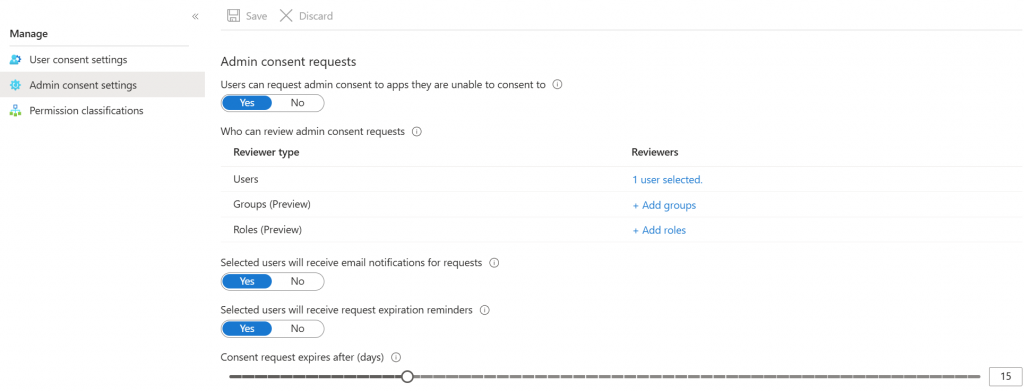
Here is where you allow the notification to appear that blocks the apps and asked the user if they want to make a request to use the app.
Choose the user, group, or role that you want the request to go to. The request will be delivered to an email address. If you are using a helpdesk ticketing system provide it with the inbound ticket email address of that system.
Choose to provide email notifications back to the user and how many days the request will be good for before it expires. Remember that the user feels that they need this app to do their job, so you don’t want the request to hang out there for too long.
Optional low risk pre-approval
If you are concerned about the volume of requests you may receive, you could optionally pre-approve a limited set of low-risk permissions.
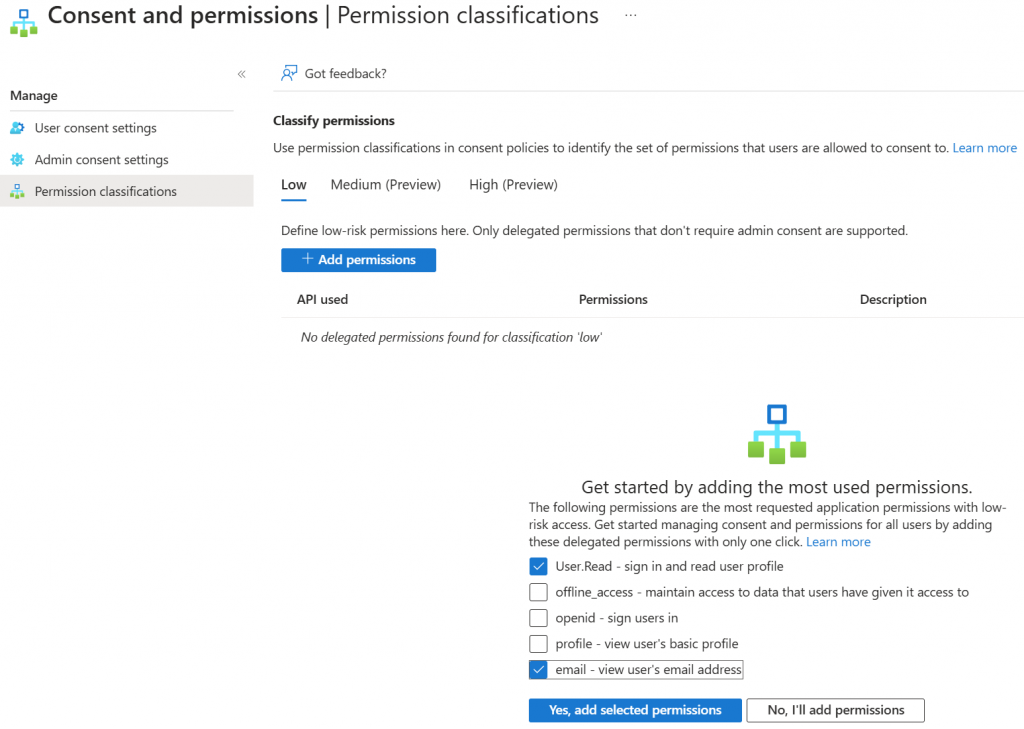
This is done in the Permission classifications menu. Make sure that Low is selected, then check the suggested permissions that you want to pre-approve. If a user wants to use an app that only uses these permissions, they won’t need to make an admin request.
Microsoft will suggest a permission set, but notice that these are the most used permissions, not necessarily the least permissive or safe to grant permissions. Select what you are comfortable with. Then click Yes, add selected permissions.
For this to work you’ll need to go back and select Microsoft’s recommended setting in the first step. But before you do that take a look at what apps have already been granted permission. This will help you understand the extent of the problem that you’re dealing with.
Reviewing apps previously granted permission to the network
As a security maintenance task, we do need to review apps that have permissions in our network and determine whether they are still in use or if they can be removed.
Back in the Enterprise Applications menu, Select All Applications
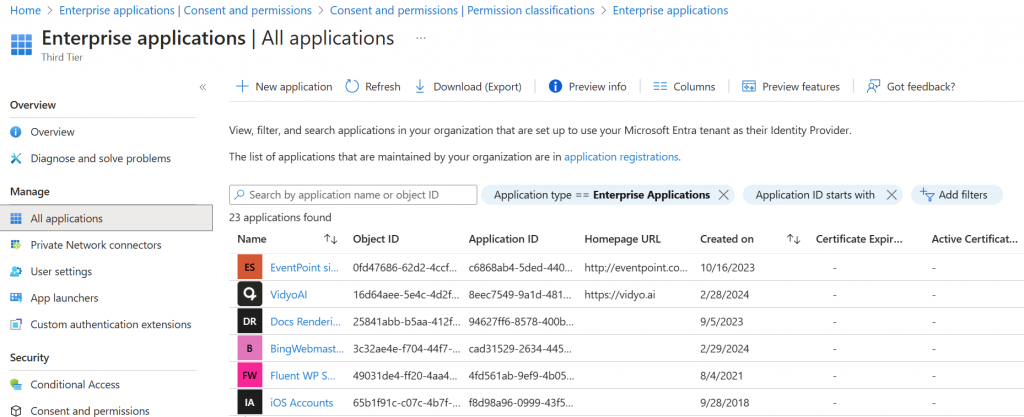
All of the applications you see here have previously been granted permissions to the network. Click into the app to review the permissions and the sign-in logs.
Conclusion
Good application tracking and hygiene is a critical part of security management and yet many businesses have missed these critical configurations and maintenance tasks. It’s not difficult to get this configured and added to your routine.




