Today I was in a meeting and my name showed up as Amy Otter Pilot. This was alarming to me because I was not aware of having an Otter subscription. Apparently, I had a free account because of my curiosity when I was sent a meeting recap from another person. I clicked to see what this was all about. But in today’s meeting, a person I met with was sent a meeting recap from “me”. Otter had joined a meeting that I was invited to and then emailed them that person a recap of our meeting. I was very disturbed by this event.
I don’t have an Otter app installed on my computer, nor is it a browser extension, nor is it an add-in for Outlook. So how is it doing this? OAuth.
What a great follow up to my recent blog post, How to secure your network from OAuth permissions (thirdtier.net). As an administrator, I was left subject to OAuth installation, but you should block your users from setting up OAuth accidentally or intentionally. OAuth permissions are permanent, so they deserve careful control.
How to Remove Otter
There are two parts to removing your Otter account. Part one happens on the Otter.ai website and the second part happens in Defender for Cloud Apps.
Part 1: Visit https://otter.ai, when I did, I was not asked to authenticate it simply opened into my account, the account I was not aware of setting up.
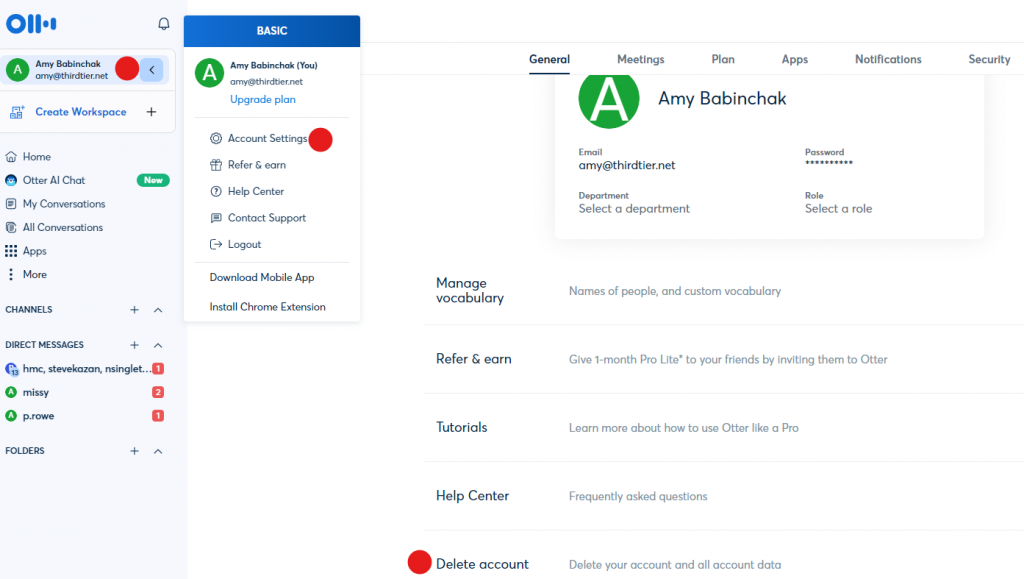
Follow the red balls above. Click on your account and select Account Settings. Look to the bottom on the main panel to find the Delete account option. Once you click to delete your account, you are asked to authenticate. Do that and then your account will be deleted from the Otter account page.
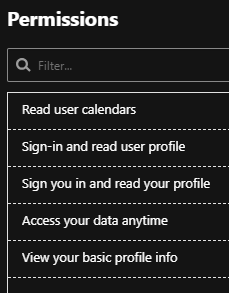
Part 2: Unfortunately, deleting your account from Otter does not revoke its permission to your mailbox. Otter installs itself as an OAuth app in your network but does not remove itself. Below you see the permissions that it has been granted.
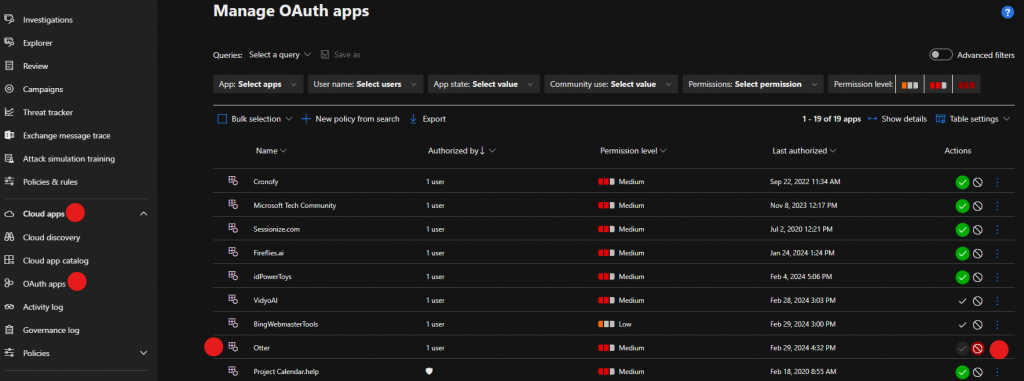
To block the Otter OAuth, visit https://security.microsoft.com and scroll down into Cloud Apps and select OAuth Apps. In the main screen, look for Otter and select Block.
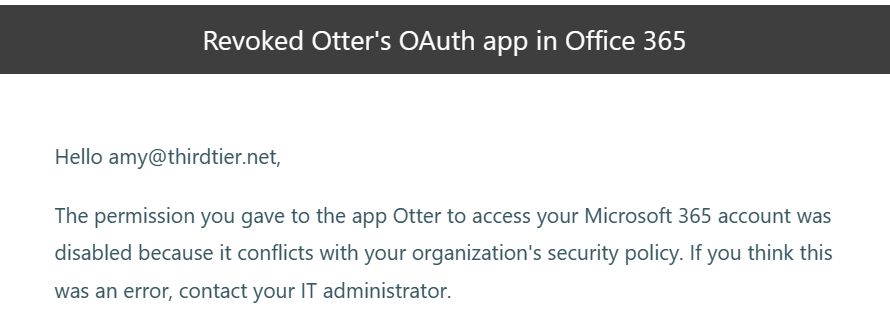
Once you’ve blocked Otter, users that have the permissions assigned will get an email letting them know that Otter has been blocked.
Recommendation: Take special care with these meeting services. There are many important issues to consider including compliance, privacy and permissions creep.
All we do is support IT professionals. Security community, MSP Legislation community, EndPoint, Defender and Lighthouse community, Peer groups, courses, papers, Business consulting and more. https://www.thirdtier.net





7 thoughts on “The invasive Otter”
Hello Amy
Thank you very much for this blog. I do not understand how what is occurring with this Otter can even be remotely legal and I hope there is a class action lawsuit to sue their butts off. I had been in a board or directors meeting where the executive was using this Otter to take notes and I was interested in it so I went to the website to look into it. All of a sudden Otter starts showing up in my Teams meetings and I get emails from them with half of a transcription of the minutes – if I want to “take advantage of this great app, I need to create an account and set up a subscription service”. I DID NOT create a log in / password and I find this very intrusive and abusive. I have Googled how to get rid of it and I can’t believe how difficult it is to attempt to remove and I still do not understand. Above you give a 2 part exercise to get rid of it. I didn’t sign in as mentioned and don’t want to so I don’t know how this part even works. In Part 2 I cannot find this Cloud Apps / Manage OAuth you refer to?
Here’s the worst of it, Dave. Otter isn’t the only app that behaves this way. They all do. And you will need to purchase additional licensing for your Microsoft 365 account or Google account, which ever you are using, in order to gain access to the settings to manage oAuth apps and their permissions. For Microsoft 365 you’ll want to get a Defender for Cloud Apps license or Microsoft Business Premium, which comes with it.
Let me know when you see the class action suit, hours of my time looking for answers, several off site tech help request and affects how others look at our security.
FYI take a look at individual users appdata, local, google, chrome, user data there may be a folder in here for otter.
Good steps to disable, would not have found it
How do I remove permissions if it’s a gmail account?
GSuite contains similar provisions for removing oAuth permissions. A straight up consumer gmail most likely does not.